User Account Policies
General policies for user accounts include lockout settings, password policies, and custom user fields.
General
To configure general account policy settings, go to Authentication > User Account Policies > General.
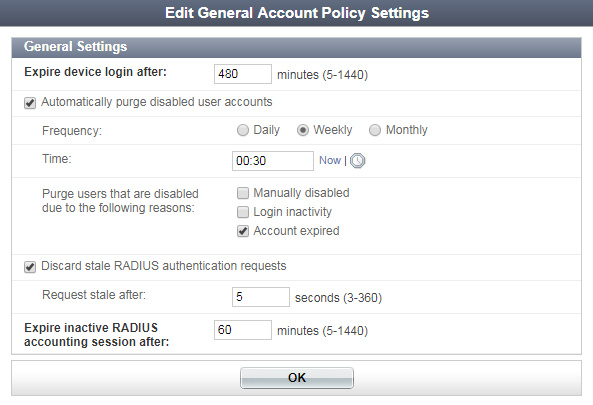
Configure the following settings:
Lockouts
For various security reasons, you may want to lock a user’s account. For example, repeated unsuccessful attempts to log in might indicate an attempt at unauthorized access.
Information on locked out users can be viewed in the Top User Lockouts widget, see Top User Lockouts widget.
Currently locked out users can be viewed in Monitor > Authentication > Inactive Users, see Authentication.
To configure the user lockout policy:
- Go to Authentication > User Account Policies > Lockouts.
- Configure the following settings, then select OK to apply any changes:
Passwords
You can enforce a minimum length and complexity for user passwords, and can force users to change their passwords periodically.
For information on setting a user’s password, and password recovery options, see Editing a user.
Go to Authentication > User Account Policies > Passwords to configure password policy settings.
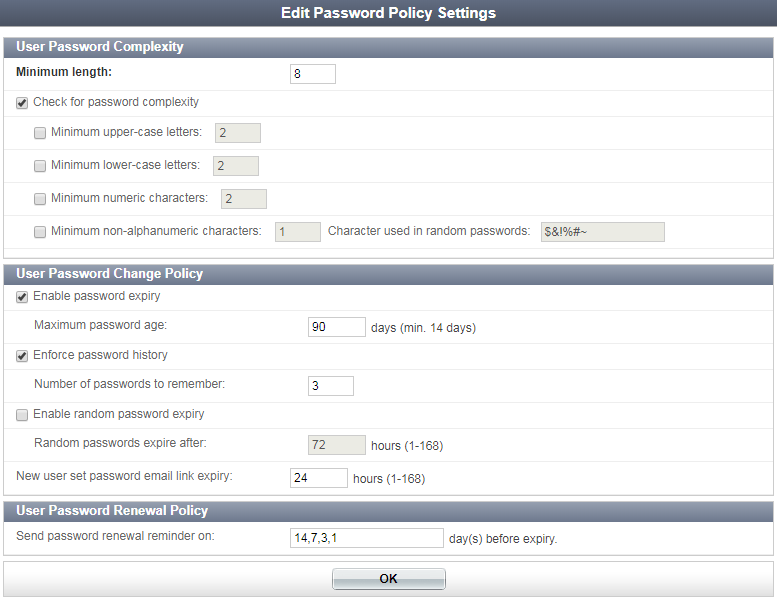
To set password complexity requirements:
- In User Password Complexity, enter the minimum password length in the Minimum length field.
|
|
The default minimum length is 0, which means that there is no minimum length but the password cannot be empty. |
- Optionally, select Check for password complexity and then configure the following password requirements as needed:
- Minimum upper-case letters
- Minimum lower-case letters
- Minimum numeric characters
- Minimum non-alphanumeric characters
You can configure which non-alphanumerical characters may be used in random password generation by entering them in the Characters used in random passwords field. - Select OK to apply the password length and complexity settings.
To set a password change policy:
- In User Password Change Policy, optionally select Enable password expiry, then set the maximum allowed password age in the Maximum password age field.
- Optionally, select Enforce password history to prevent users from creating a new password that is the same as their current password or recently used passwords.
- Optionally, select Enable random password expiry to force randomly generated passwords to expire. Then, enter the length of time after which a randomly generated password will expire in the Random passwords expire after field.
- Select OK to apply the password change policy settings.
The default maximum password age is 90 days. The minimum value allowed is 14 days.
Then, enter the number of password to remember in the Number of passwords to remember field. New passwords must not match any of the remembered passwords. For example, if three passwords are remembered, users cannot reuse any of their three previous passwords.
The default randomly generated password expiry age is 72 hours. The value can be set from 1 to 168 hours.
To set a password renewal policy:
- In User Password Change Policy, enter the password renewal intervals in the field available, separating each entry by a comma.
- Select OK to apply the password renewal policy setting.
The default is every 14, 7, 3, and 1 days.
Custom User Fields
Custom fields can be created to be included in the user information of local users. See Local Users for information about creating and managing local users.
To edit custom fields, go to Authentication > User Account Policies > Custom User Fields. A maximum of three custom fields can be added.
Tokens
As of FortiAuthenticator 4.2, all FortiToken settings have been moved here to be configured and controlled separately from the general user account policy settings. Additionally, now you can configure the FortiAuthenticator to allow the Windows Agent to cache future tokens for users when they're offline by using the Enable offline support setting.
To configure token policy settings, go to Authentication > User Account Policies > Tokens.
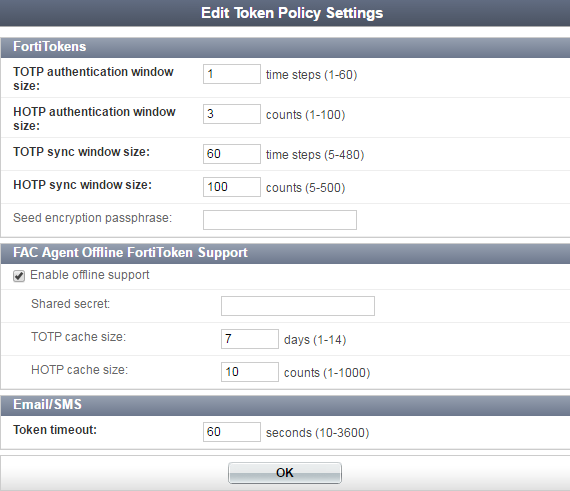
|
|
Note that, as of FortiAuthenticator 4.3, the offline HOTP cache size limit has been increased from 100 to 1000. |
Configure the following settings:
